Asymmetric Key Cryptography
I know, it’s a mouthful!
I never thought I’d understand asymmetric cryptography, partly because I tend to stay away from REALLY complicated stuff, and partly because of the math involved. It’s really complicated math. Really.
But it turns out that it is possible to tame this beast!
Background
The opposite of asymmetric is of course symmetric. Symmetric key cryptography is much more comprehensible for a human brain, since it depends on a shared key, that is used for both encryption and decryption. However when the key is compromised or lost, anyone can tap in on the conversation. Not good!
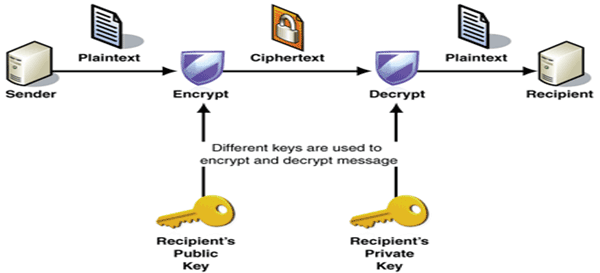
“Asymmetric key cryptography” works completely different and relies on some very complicated (and pretty cool) math to generate two keys: I’ll call them PRIVATE-KEY and PUBLIC-KEY.
Anything you encrypt with PRIVATE-KEY can only be decrypted with PUBLIC-KEY, and anything encrypted with PUBLIC-KEY can only be decrypted with PRIVATE-KEY.
Using this method you can safely communicate with anyone, by showing your PUBLIC-KEY, and hiding your secret PRIVATE-KEY. All you need from your counterparties are their PUBLIC-KEY.
And yes, I’ll admit that it’s kind of magical that such a thing is even possible.
They say it’s got something to do with really large primes, but I doubt it. It’s more likely magic.
Public keys and private keys
As I stated above, you make your public key available to anyone, and you keep the other key private and secret. Hidden and protected.
In Linux, you can create this pair using:
ssh-keygen -t rsa -b 4096 -C "your_email@example.com"
and of course you replace “your_email@example.com” with…. your real e-mail. A shocker that!
Now you will have two files in ~/.ssh id_rsa and id_rsa.pub. I’ll leave it as an excercise to figure out which one is the public one!
Anyway, my public key looks like this:
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQDAFWFzkNun8aUNJFYpbYJYnZ9KjKVnirs7Nh31vEHz6il75RWPY1t│0.456428 a2RjFxsZ/W0HK21ePqVCfjtZL20TdVldcMRRbrdl0Gi0zSpRJSxx9+I/gcQQfjiKzFcgbngzoN+wRRT3aaSZDTpwKfy│0.45713 R2pX3NHmltgpO5ve0kKdeErLnBzfIb3qUDHqGMv0ZqbfkRMLpyatnLyD6KWiIGabX8VeTDy2CZuU2vAF4pGzbFYjolj│-------------- WVLhlSdV4iQbiy0cUfFnYl/2Am0m95Gg0DJyCPHFA5ZHcgLhIKExOk24sEAc8W2Fw3lqdAR4yfNzO8eTlVHxA+zsCO7│0.11 aiZUvAZYoDYkpHpJxrP0vJu7cCp+umB9DLYl1/TC4Lt5bQXYfSG8U+gMyk14u4mozHu+QgYucNSSPe5ErenpmWSU4J0│0.111733 iX9o6SZk3g4exMi8fD+V0YgCB5A/bo9k/Qz3JC9E/83vdgLCaE2xQ8K4aoRLwaQ3wIfRuiRlsKdJNcCJRzaaV2LAHVF│0.109778 TOntEM+PaUFpqV4xr2jhLFEuiVuQrUaltwxOYKQEd4/Q+Eo2sBs4toXfeIngxw4wcoS7VQ8U8u6UiANzSuuEdTOLfBw│100/100 [==============================] - 0s 201us/step BYKvjfvHXZqt+wGb3kSSgpj5tLziEwadSpaUMZmGebFb/h6J+eLUWGzfobgPkr8Utq8XsYfZaLzXYwTAliv2w== pet│ er.andersson@fsh.se
You’re welcome to add it!
If I encrypt something with my private key, you can absolutely confirm that only I could have encrypted it, by using my public key to decrypt it.
Encrypting message, in practice
But how do you know the decryption worked? After all if XY5623jhd was decrypted to 2341.04 how do you know that it has some meaning and just isn’t random numbers?
Well one thing you can do is included a hashcode in your message.
Let say I have this message “The secret keyword is flowerpot” that I want to send to my agent in Russ….iastan.
echo "The secret keyword is flowerpot" > secretmessage
I calculate a MD5 hash on that message
md5sum < secretmessage 5a19f24b0131493718df2b3bc47d42cd -
And I could put together a message using the above like this:
md5sum < secretmessage > secretmessage.withmd5 cat secretmessage >> secretmessage.withmd5
We now have the MD5 hash in the first line the then the rest of the message. So anyone decrypting this message can check the MD5 and verify that the decryption worked. ( In reality, this is not how it works, I just wanted a really simple example of the process).
I won’t go into how to setup the actual encryption, there are several ways of doing that, look here https://www.howtoforge.com/tutorial/linux-commandline-encryption-tools/ for an example. PGP and GPG are common tools but there are a multitude of plugins for email applications and similar.
TL:DR
The executive summary is therefore:
1) When you encrypt something with your PRIVATE key, it can ONLY be decrypted using your PUBLIC key. Thereby anyone who can decrypt it, knows that you have sent it (since you had the private key).
With this process anyone can decrypt the message (using your public key) and thereby also verify that YOU sent the message. It’s not a fraud. However ANYONE can read what you wrote. But it authenticates YOU as the sender.
2) When you (A) want to send something secret to another party (B), for his eyes only, you can use B’s PUBLIC key to encrypt the message, since then you know that only B can decrypt it using his PRIVATE key.
With this process, only B can decrypt the message. However B cannot know WHO encrypted it, since B’s PUBLIC key is….. well public.
The neat thing is that you can use other peoples PUBLIC keys to verify that they are who they say they are, and you can let people send encrypted data to you, that only you can decrypt.
And it works the other way too! By combining these two encryption stages, you can at the same time guarantee who you are (A) using (1) and guarantee that only the other party (B) can decrypt it using (2).
It seems complicated at first, but if I can understand it, anyone can!
The possibilities are endless
This same process can be used for more than electronic messaging, it can also be used for any system where you want to lock down two entities, like for example chains in a blockchain. It’s an incredably versatile technology, just don’t ask me how it works, there’s probably some magic involved.